As the industry moves into further digitization of patient care, health care organizations must keep data and operations secure.
Cybersecurity health care trends: Key takeaways
Everyone throughout the organization must play a role in preventing cyberattacks.
Infrastructure improvements, appropriate training and ongoing education can address security vulnerabilities.
When many functions of health care services and providers went virtual during the pandemic, consumers began to see the value and flexibility of this change, as did many hospital employees. The industry has moved forward with a hybrid model of in-person and virtual services and remains vigilant about securing patient data due to this new decentralized environment.
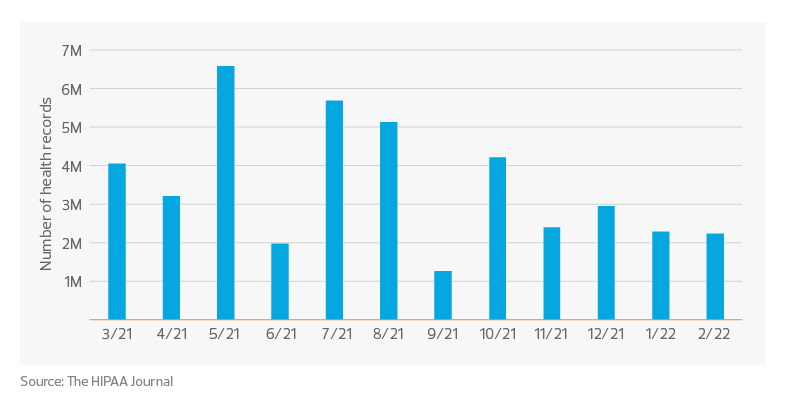
At the same time, hospitals and health systems have become prized targets for cybersecurity attacks. According to the 2022 Healthcare Data Breach Report, there were 11 reported health care data breaches involving more than 1 million records and a further 14 additional data breaches of over 500,000 records in 2022. Many of those breaches were hacking incidents involving ransomware or attempted extortion.
As the industry moves toward further digitization of patient care and services, and grows with competition, health care organizations must strategize how to keep their patient data and operations secure from threats.
The desire and need to acquire and use data more aggressively in serving patients and in the operations of the health care environment requires a comparable investment in their information security and privacy capabilities to meet the challenge of maintaining secure and available systems and reliable information.
Vetter indicated that any breach of systems can cause a disruption in patient care and a loss of patient confidence in the organization, both of which can halt operations or move patients to seek care elsewhere.
U.S. health care records breaches in the past 12 months
Impact of cyberthreats
Cyberattacks on electronic health records and other health care systems pose a risk to patient privacy because hackers access patient health information and other sensitive information. By failing to keep patient records private, organizations could face substantial penalties under HIPAA’s privacy and security rules, as well as potential harm to their reputation within the community. Losing access to medical records and lifesaving medical devices, such as when a ransomware event holds records or information hostage, will hinder an organization’s ability to effectively care for patients. Hackers’ access to private patient data opens the door for them to not only steal the information, but also either intentionally or unintentionally alter the data, which could lead to serious effects on patient health and outcomes.
In addition, cyberattacks are proving costly to hospitals and health systems. The average health care breach now costs more than $10 million, according to an analysis by IBM Security. Malware, phishing and ransomware are all common types of cyberattacks posing a threat. Even with this knowledge, organizations continue to get breached, however. Since 2014, cyberattacks have dramatically increased from 14% to 69% in 2020, according to the U.S. Department of Health and Human Services.
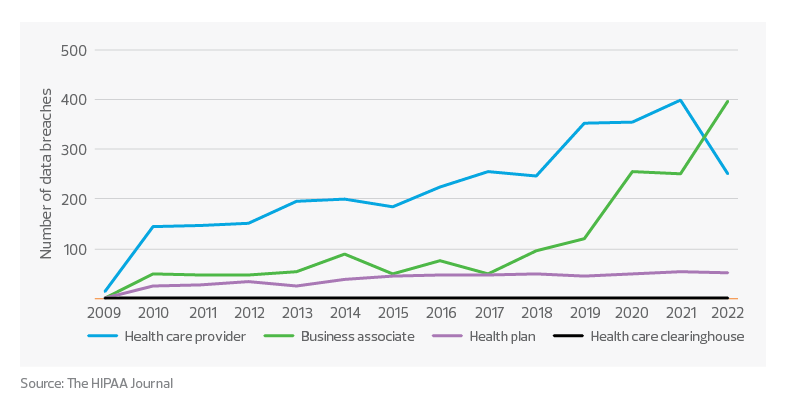
According to the Healthcare Data Breach Report, the data also shows multiple channels of vulnerability through which cybercriminals can infiltrate a health care organization’s systems. In recent years, health care systems started outsourcing more of their administrative tasks to offset costs and labor shortages, a move that added third-party vulnerabilities. To address these concerns, organizations should establish stronger infrastructures and monitor capabilities to prevent liabilities and hold users (and business associates) accountable.
The industry is at a point where hospitals and health care organizations, including smaller physician practices, can no longer sit on the sidelines waiting for a breach to happen. Everyone needs to play a role in preventing cyberattacks, especially now that the industry has established PHI exchanges and is promoting data interoperability.
Data breaches at HIPAA–regulated entities
Addressing vulnerabilities
Organizations can address ongoing security vulnerabilities by focusing on the following areas.
Infrastructure
Maintain strong data security practices by monitoring access permissions and regularly reviewing role permissions based on user responsibilities. For example, with patient insurance information and billing records, limiting access to only those responsible for processing insurance claims and billing patients for outstanding balances helps secure the data and limits exposure. The same is true with patient records that show diagnoses, treatment plans or prescriptions. Typically, only attending physicians and nurses need access to this data. If other health care professionals need access, it should be controlled on a case-by-case basis and limited to just the specific data required.
Fortunately, the many advances in cyberdefense technologies and practices can greatly reduce an organization’s risk. Many health systems have prioritized developing the processes and capabilities, either in-house or with third-party support, that represent leading-edge data security. The more common types of solutions include data backup and recovery, data encryption, anti-virus/malware/spyware programs, and ongoing monitoring of reports and protocols.
Lastly, while a commitment to data interoperability provides an opportunity to reduce costs, minimizes redundancies in services and improves providers’ ability to coordinate patient care, it’s important for organizations to have established protocols for disseminating this information to patients in a secure and efficient fashion.
TAX TREND: Infrastructure investments
Organizations that develop certain IT infrastructure, including some types of software, might be surprised to find out those costs must be capitalized and amortized for tax purposes. Additionally, starting in 2023, bonus depreciation allows only an 80% first-year deduction.
Training and ongoing education
Cybersecurity training provides health care personnel with the information they need to make wise decisions and exercise appropriate caution while managing patient data. Effective cybersecurity training should help employees recognize and halt attacks before they cause damage. The employee is the first line of defense and the greatest weakness.
Another reason cybersecurity training is vital is because HIPAA mandates it. Specifically, the federal privacy rule states that a health care provider must “train all members of its workforce on the policies and procedures with respect to PHI,” and “implement a security awareness and training program for all members of its workforce (including management).” With that training in place, and repeated often, employees are better equipped to recognize situations where the use of PHI warrants special protections, such as with email or role-based access controls.
If all employees have a sense of urgency about the impact of cyberthreats and practice good cyber hygiene, the team can reduce the number of potential threats to an organization and maintain operations to provide quality care to patients.


