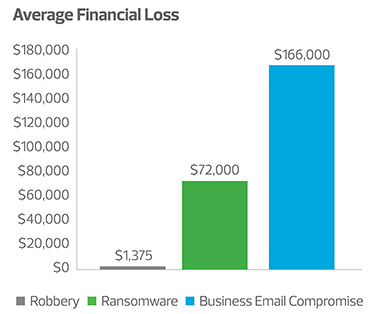
You are the target
Cyber events based on an attack against the user comprise 48% of the claims, while only 39% are related to a technical attack, such as hacking and malware. The attacks that are more focused on us, the everyday user, are more varied, and include attacks such as social engineering, phishing, staff mistakes and lost devices. Despite the everyday user generating the greater risk, most companies spend the vast majority of their time and resources on technical defenses and discount the human risks. The best risk strategies address both technical areas and user awareness and training.
There are a number of threat scenarios that can lead to a cyber incident; however, there are two primary attack types we are seeing over and over.
- Phishing: Users are often attacked through emails with links to fake websites. The attacker relies on human nature to gain user credentials and other information to gain unauthorized access to various data an dystems.
- Social engineering and stolen data: Attackers use social media and corporate websites to perform reconnaissance to develop social engineering attacks against users. These attacks are often well designed so the attacker may be able to represent themselves as a benefit plan client or an internal employee.
These deceptions are hitting benefit plans, often through bogus requests for access, demands to move funds, appeals for contact or contract information, or other manipulations. These breaches are usually considered the company’s fault, unless it can be proven otherwise. It’s worth noting that end users are most often hacked without the company’s involvement. The hacker is gaining access to the participant’s assets not by breaching the company, but breaching the user’s account directly.
What should you do?
There are a number of considerations and proactive steps that companies can take to help prevent against a cyber incident. While these proactive actions are a good start, remember that attackers continue to develop new techniques to compromise systems and gain access to critical applications that may contain sensitive information.
No organization is completely safe against cyberattacks, regardless of the efforts taken to be proactive in preventing an incident. The key is to stop an attack when it is merely a security incident before it becomes a full-blown data breach.
- Ransomware—to pay, or not to pay: The question that is frequently asked when a company suffers a ransomware attack is “Should we pay the ransom?” The decision of whether to pay ransom when yourcompany has been infected with ransomware is largely a business decision. While there is no correct answer with how to proceed, there are some key points to consider:
- Do you have a way to pay the ransom?
- Are there viable backups?
- How urgent is the need or timing to become operational again?
- What types of data are encrypted? Not all data handles the encryption and decryption process well.
- Ultimately, what is the cost/benefit analysis of paying the ransom versus restoring or completely rebuilding your environment?
- Social engineering awareness training: Companies need to make sure that they are implementing security awareness training to everyone involved in the plan administration as well as participants of the plan. Many employees simply do not understand the methods used in social engineering, and this makes them vulnerable to fall victim to such attacks. Do not excuse executives from this type of training; they are the most common targets and can be just as vulnerable. Design the awareness training to include information that you will never ask (i.e., user name and password, account number), as well as how communication will be handled (i.e., you will never call and ask for information). It is also important to make sure that everyone is aware of how to report a potential social engineering or phishing attack.
- Incident response preparedness: A response plan is only as effective as the supporting components to make it work. Management should recognize when it is in over its head. The urge to try to manage it internally is overwhelming, but the appearance of delaying a response can cost companies in lawsuits and fines later. It also often leads to the destruction of evidence of the attack, but not the elimination of the hacker from the environment. Companies should do a triage to stop the attack from getting worse, then take their hands off the keyboards and call in the incident response team.
- Insurance: This is the last line of defense. Companies should not count on cyber insurance being covered under a general policy; it is often specifically stated that a separate, stand-alone policy is required for cyberincidents. Make sure the policy is covering the most common costs (e.g., ransom payments). Management should make sure that contracts cover fines and that the sublimits are reasonable.
Even despite these proactive steps, attackers continue to develop new techniques to compromise systems and gain access to critical applications that may contain sensitive information. No organization is completely safe against cyberattacks, regardless of the efforts taken to be proactive in preventing an incident. The key is to stop an attack when it is merely a security incident before it becomes a full-blown data breach.