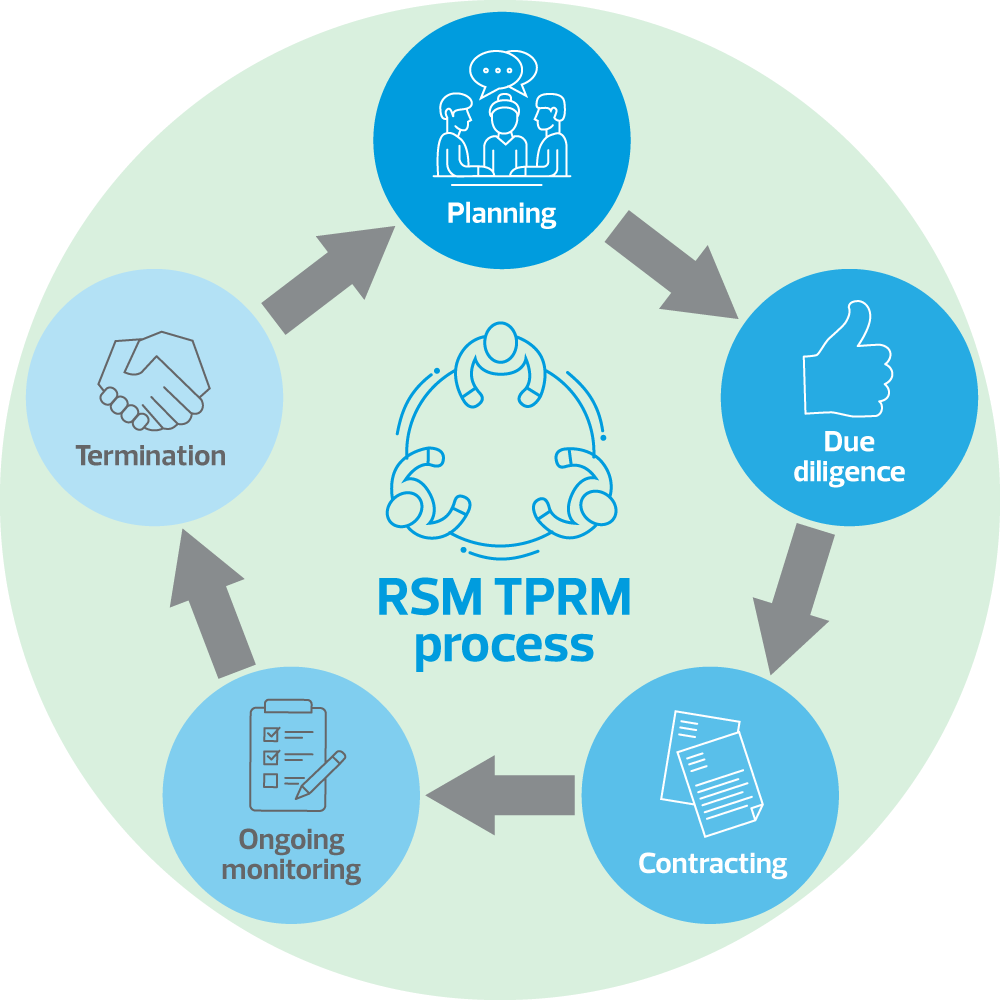
Third-party risk management (TPRM), also called vendor risk management, is the practice of evaluating and mitigating risks introduced by vendors (suppliers, third parties, or other business professionals) before establishing and throughout a business relationship.
In today’s complex market, companies often turn to specialized contractors and third-party service providers to focus on core activities. However, many organizations have learned this practice comes with a certain measure of risk. Whether a professional service provider makes an honest mistake or a technology service provider encounters a cyberattack seizing operations, companies must address the introduction of various levels of risk.