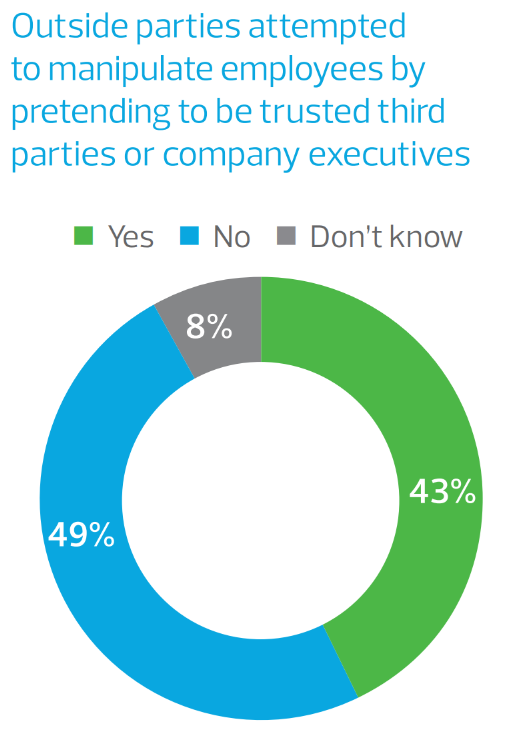
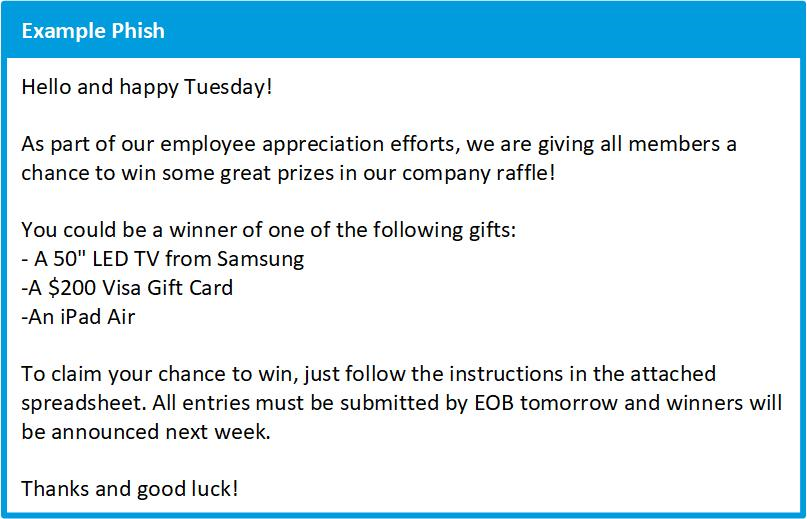
Aware of these dangers, many companies are taking steps to protect against phishing attacks by conducting awareness training for employees or performing internal phishing campaigns to test their defenses. The central element of a strong phishing awareness training program is education. You need to know both how to detect a phish and how to properly report it. Therefore, we have reviewed the awareness training programs at a wide variety of companies to provide you with the most effective methods for protecting yourself and your organization against this pervasive and persistent risk.
Spotting a Phish
The first step in phishing awareness is recognizing the signs of potential phishing. These signs include:
Unfamiliar or misspelled sender address
Attackers often use false sender addresses, particularly if controls (such as an SPF record) are in place to prevent spoofing from internal addresses. Be on the lookout for addresses ending .corn instead of .com. Also be on the lookout for addresses ending in .net, as well as unusual elements added to the domain such as @example.suspicious.com instead of @example.com.
Tip: When in doubt, Google a suspicious domain name to determine whether it is tied to any known phishing schemes.
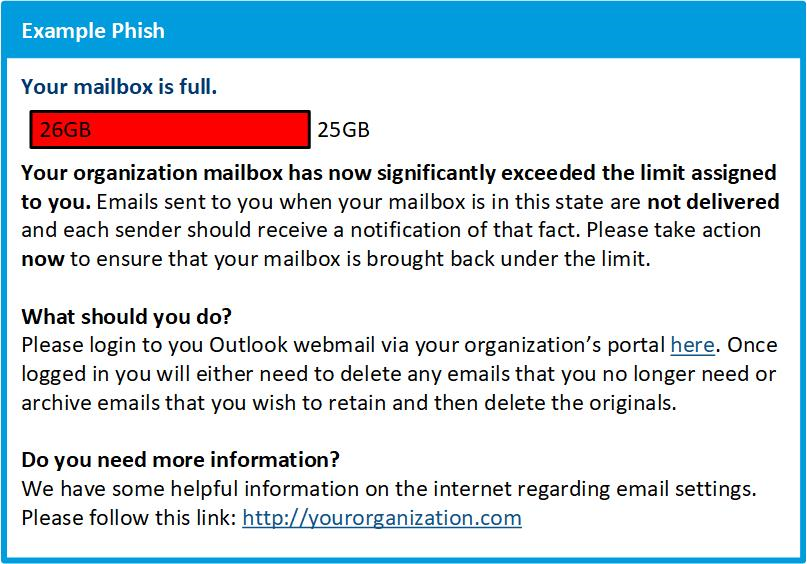
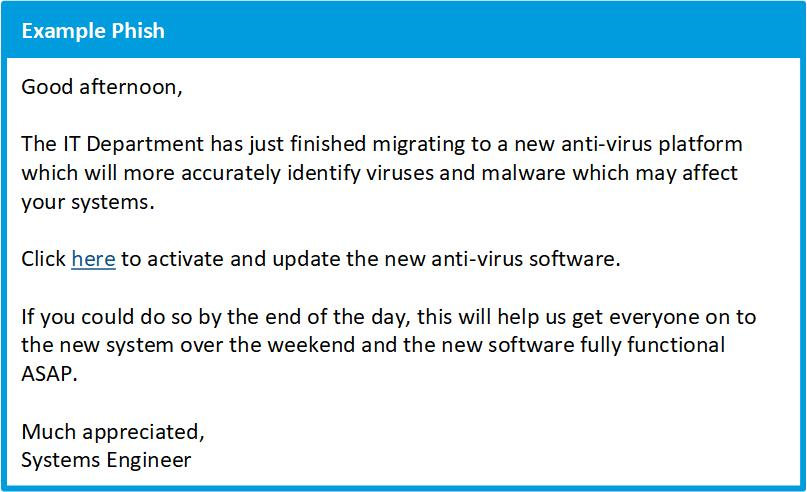
Unexpected or questionable requests
Any emails asking you to perform an action for which you have had no prior notice (such as upgrading to a new system) should raise alarm bells. Though hackers are tailoring phishes to specific lines of business and using scenarios that people in your organization may have encountered before, it’s still better to verify with a supervisor before clicking (particularly if the request is completely unexpected).
It’s especially important to be skeptical of emails asking you to authorize major transactions or transfers. Instead, users should verify such actions in person or through channels previously established as legitimate.
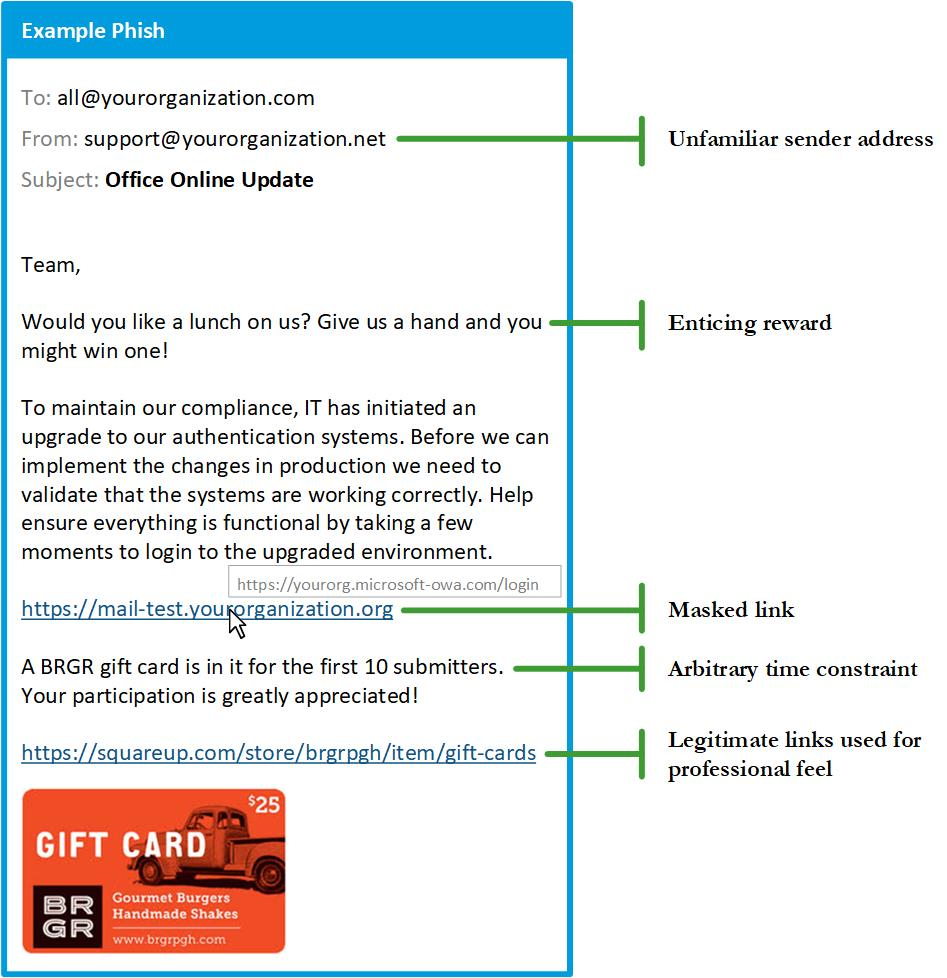
Masked links
Attackers may mask malicious content in a seemingly innocent hyperlink. However, hovering over the link reveals where it will actually send users. Ask yourself: Does the link direct to an unfamiliar site? Does it take you to an unsecured site (HTTP) when it should be directing to a secure site (HTTPS)? Utilizing link scanners can also verify a link’s security without having to navigate to the site.
Suspicious attachments
Many phishing emails are often designed to trick you into downloading a malicious document and enabling macros. Attackers embed macro-based malware in Microsoft Word documents and Excel spreadsheets and design a convincing pretext to convince users to launch the file. Always double-check the source of the file and be extremely cautious about enabling macros.