The Broadband Equity, Access, and Deployment (BEAD) Program—part of the Infrastructure Investment and Jobs Act (IIJA)—is designed to expand access to broadband infrastructure within rural and underserved communities. Underpinning this initiative is the requirement that subgrantees develop and implement a risk management plan that adheres to the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity. To meet this requirement, a subgrantee must have a cybersecurity risk management plan as well as a separate cyber supply chain risk management plan that is operational or ready to be operationalized prior to the allocation of funds.
BEAD cybersecurity requirements for grant subrecipients
The federal government is currently distributing broadband infrastructure grants to internet service providers through the American Rescue Plan Act. However, the BEAD Program significantly expands the requirements for grant subrecipients in a variety of areas, including environmental policy and climate resiliency, Build America Buy America and cybersecurity program considerations. These provisions will require organizations planning to utilize BEAD funding to document and implement cybersecurity programs in alignment with multiple industry-recognized frameworks from NIST.
Breaking down a plan for compliance
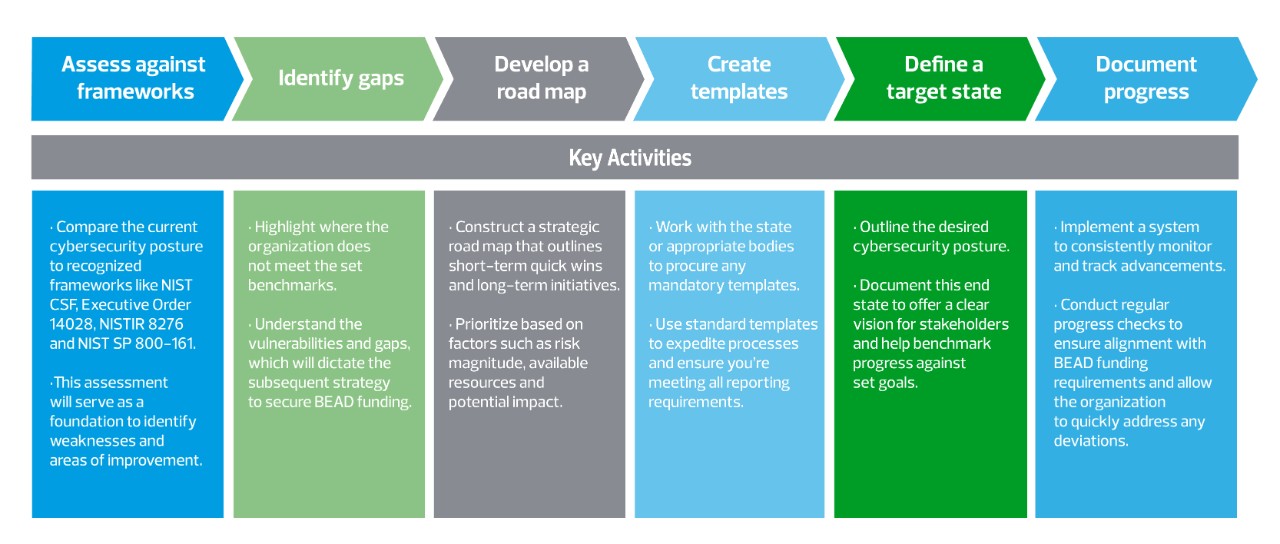
Consideration 1: Documenting two cybersecurity plans
To receive grant funds, eligible entities need to ensure that subgrantees—defined as entities that receive grants from an eligible entity to carry out eligible activities—meet the following cybersecurity requirements outlined in the Notice of Funding Opportunity:
Cybersecurity risk management plan
This document transcends mere paperwork; it serves as a strategic road map, intricately designed to align seamlessly with the NIST Cybersecurity Framework (CSF). The cybersecurity risk management plan must adhere rigorously to the standards articulated in Executive Order 14028 and clearly capture each of the following:
- A threat landscape analysis specific to the region
- Risk assessment methodologies adopted
- A detailed mitigation plan, addressing both current and emerging threats
- Response and recovery strategies, detailing steps following a potential breach
Cybersecurity supply chain risk management (C-SCRM) plan
The subgrantee is required to have a C-SCRM plan based on key practices discussed in NISTIR 8276 and guidance provided by NIST SP 800-161, and must clearly state each of the following:
- A detailed assessment of external product and service providers
- Proactive measures to vet, monitor and manage suppliers
- Protocols for immediate action if a threat emerges from a vendor
Subgrantees are mandated to submit both of these plans to the eligible entity before fund allocation, and should provide updates when making modifications.
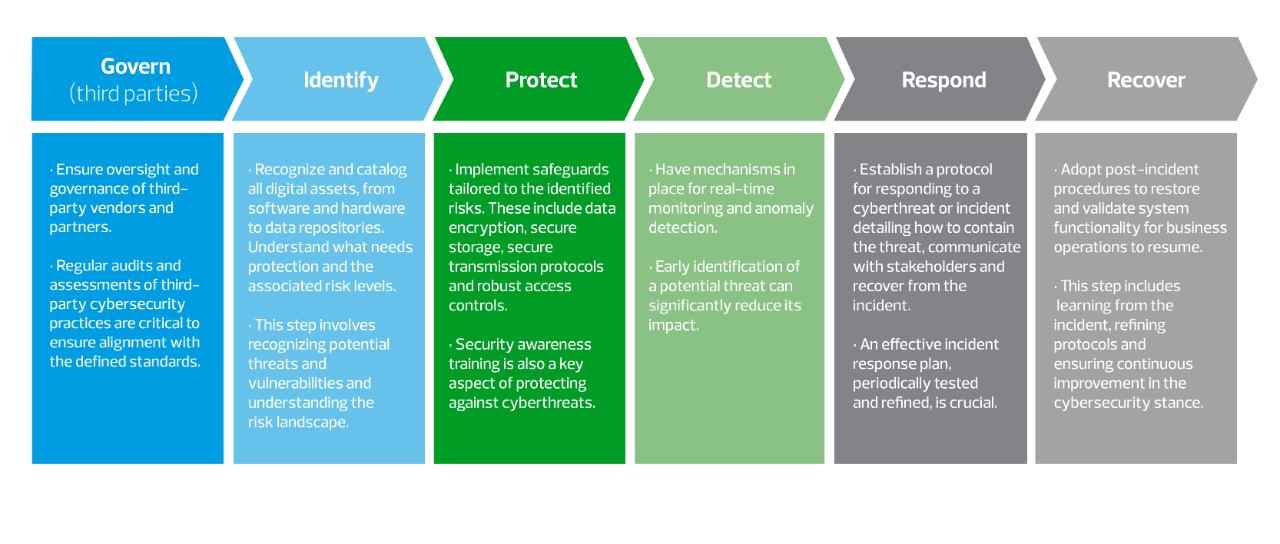
Consideration 2: Aligning programs to leading standards
While documentation is a key requirement, implementation of the two plans according to the standards set by the governing publications is also important. The following table demonstrates which publication(s) govern each plan.