Level 1
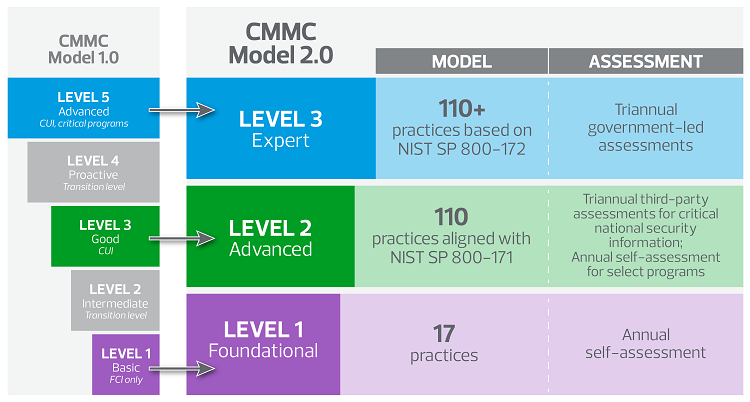
Level 1, the foundational level, now enables organizations to demonstrate compliance through annual self-assessments. With just 17 key practices, this allows for lower-risk organizations to achieve an affordable path to CMMC 2.0 compliance.
Level 2
Level 2 (formerly level 3) is CMMC 2.0’s advanced level, geared toward organizations handling CUI. Contractors now must comply with 110 practices (rather than the additional 20 practices previously added to the framework). Contractors that hold “critical national security information” are required to leverage CMMC third-party assessment organizations (C3PAOs) for triannual assessments, while a select set of programs will allow for annual self-assessments.
Level 3
Level 3 (formerly level 5) will require more than 110 practices, based on NIST SP 800-171 standards. Additional requirements will be based on NIST SP 800-172 Enhanced Security Requirements for Protecting CUI. This means 35 new enhanced security requirements may be added across existing domains. Additionally, level 3 will now be reviewed through government-led triannual assessments.
How does this affect my business?
While change is constant as cybersecurity threats continue to evolve, organizations must maintain their adaptability to respond quickly when necessary. These minor changes are more distinctions rather than drastic differences. There is a significant shift in language and process, but little change to the expectations on businesses.
If you work with the DOD, your organization is still required to design and implement a cybersecurity program aligned to NIST 800-171 during this transition period. It is crucial to leverage experienced industry advisors such as RSM to ensure your eligibility to bid on future DOD contracts that will require CMMC in the not-too-distant future. The timeline is the interesting point, as it will take 9‒24 months, based on the DOD estimate, to fully implement CMMC 2.0 and see the mandatory requirement appear in all solicitations. That said, early adoption is strongly encouraged says Deputy Assistant Secretary of Defense for Industrial Policy Jesse Salazar.
While your organization may be one of the lucky few that handles data types that will allow you to self-attest, currently there is no guidance on which data types will qualify for self-assessment. In a critical development, the new Department of Justice (DOJ) Civil Cyber-Fraud Initiative gives the DOJ the ability to pursue false claims and press charges against federal contractors who are not aligned to NIST SP 800-171 and not following their federal contractual agreements.
While the CMMC Authorization Board (CMMC-AB) is aggressively looking for qualified third-party assessors to meet assessment demand, your organization should seek professional assistance now to ensure proactive cybersecurity risk management and alignment to the DOD’s expectations.
Should I still use a third-party assessor?
Third-party assessors provide an unbiased perspective on your environment and support your business’s ability to define an effective and efficient road map to progress toward CMMC compliance. Third-party assessors are often some the most knowledgeable and agile parties involved in the DOD’s requirements and guidance. Third-party assessors like RSM are intimately familiar with the NIST SP 800-171 requirements and the variety of strategies businesses just like yours can use to meet these requirements in a timely, cost-effective manner.
At RSM, we work with organizations like yours every single day. We know what it takes to create and maintain a mature cybersecurity program, and we know how to translate that practice into CMMC certification.
So, what should I do next?
In order to prepare for CMMC 2.0, consider the following simplified next steps:
- Create a contract inventory to determine which contracts include the Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 clause and identify when contract recompletes are pending.
- Identify the flow of CUI and the covered contractor information systems, including third-party subcontractors.
- Conduct a gap assessment against NIST SP 800-171 requirements.
- Develop a POA&M road map to facilitate the remediation of any identified gaps.
- Be prepared to submit your NIST SP 800-171 score and expected POA&M completion date to the Supplier Performance Risk System (SPRS) database upon request.
- Remediate your gaps and update your SPRS submission as your organization’s cybersecurity posture improves, at least on an annual basis.
- Maintain an effective cybersecurity risk and compliance management program.