For industrial companies, weak cybersecurity can endanger factory systems or power plants.
Key takeaways
Businesses should tailor their cybersecurity controls and protections to the risks they face.
Strong risk management practices integrate IT and OT issues with broader enterprise risks.
For those who work on or near a factory floor, safety protocols have long been a critical priority; appropriate personal protective equipment like hard hats and steel toe boots are essential forms of protection around machinery and production lines.
But the concept of safety for manufacturers has evolved well beyond the physical. As manufacturers become more interconnected—combining traditional information technology (IT) functions, new Internet of Things (IoT) devices and operational technology (OT) on the factory floor—strong cybersecurity measures and thorough risk management are paramount. Further, companies can draw parallels between safety and cybersecurity for personnel who have long understood the value of safety but don’t yet see the value of cybersecurity.
Companies and personnel acknowledge the importance of personal protective equipment and have accepted the costs and occasional inconvenience associated with it to prevent infrequent but potentially catastrophic consequences. Similarly, rightsized cybersecurity practices can help to significantly reduce cyber risk while minimizing cost and disruption to the business.
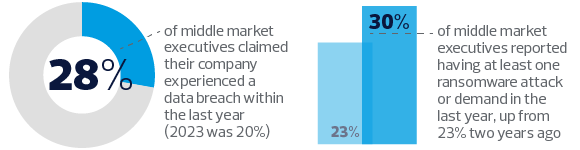
According to the 2024 RSM US Middle Market Business Index special report on cybersecurity, 28% of middle market executives said their company experienced a data breach in the last year. Thirty percent reported having at least one ransomware attack or demand in the previous 12 months, a small decrease from 35% last year, but a 7% increase from 23% two years ago.
Manufacturers—and any third parties they work with—need to raise the bar on protecting themselves. Understanding which critical information and intellectual property assets need protection from potential cyberattacks—and taking action to put those protections in place—will increasingly become a source of competitive advantage. For manufacturing companies, preventing operational disruption from attacks such as ransomware is just as important as preventing a data breach, if not more so.
“For industrial companies, cybersecurity is the new safety,” says David Carter, an RSM US industrials senior analyst. “And as more companies move their data centers into the cloud, it's changing the way they operate.”
Companies need to think holistically about these risks to successfully mitigate them, build cyber resilience and create a competitive advantage. That means not only integrating cybersecurity risk management into the broader scope of enterprise risk management, but considering how security can go beyond risk reduction to enable increased revenue and decreased costs.

For industrial companies, cybersecurity is the new safety. And as more companies move their data centers into the cloud, it's changing the way they operate.
5 steps for safeguarding your business against cyberattacks
Critical operations at stake
Some manufacturing leaders might assume that because manufacturers don’t handle large quantities of personally identifiable information—the way health care or consumer products companies do, for instance—they are at lower risk for a cyberattack. On the contrary, manufacturing is often among the most vulnerable sectors when it comes to cybersecurity breaches.
Central to these risks is OT, also referred to as industrial control systems (ICS) or supervisory control and data acquisition (SCADA) systems. For industrial companies, weak cybersecurity endangers not just data but also industrial operations like factory systems or power plants. Many manufacturers’ outdated infrastructure and increased reliance on their supply chains makes them a target, and cyberattacks on OT might hinder production, order fulfillment and, ultimately, profitability.
“OT was not designed for our digital world, and therefore, much of our critical infrastructure runs on legacy systems that are more susceptible to cyberattacks,” says Tauseef Ghazi, an RSM principal and the firm’s national leader of security and privacy. “Our critical infrastructure must not only secure these systems against attacks, but also design operational resilience for continued operations in the event of a successful cyberattack.”

Our critical infrastructure must not only secure these systems against attacks, but also design operational resilience for continued operations in the event of a successful cyberattack.
Businesses should tailor their cybersecurity controls and protections based on the risks they face. A few areas companies should prioritize include:
- Zero trust and segmentation: Introduce network restrictions to limit direct access from business networks to OT networks, and shift toward an “assume compromise” posture that increases the protections between systems on the network.
- Industrial IoT/OT: Identify where OT and IoT systems exist across company locations and develop tailored security programs and reporting on these environments, which often extend beyond the realm of IT control and/or visibility.
- Sustainable IT and OT cybersecurity programs: Evaluate the company’s cybersecurity program against industry frameworks and rightsize security activities by taking a risk-based approach to developing and implementing security controls.
- Identity and access management: Manage the risk of unauthorized access to critical data and operational processes by identifying access requirements and tools to support the enforcement of appropriate restrictions.
- Cloud security processes: Manage the security of data and systems located across various cloud service providers, identifying/remediating tactical weaknesses and implementing a cloud security strategy with appropriate governance.
- Vulnerability management: Identify weaknesses in a company’s external and internal systems before attackers do, using methods such as scanning and penetration testing.
Welcome to peace of mind
Some regulations—such as the U.S. Securities and Exchange Commission’s rule requiring disclosures about a company’s cybersecurity program and any material cyber incidents—will spur manufacturers to make their cybersecurity more robust, and the need to maintain operational resilience and stay competitive will further drive the effort for many. In Canada, proposed legislation would create a framework to protect “critical cyber systems” and “ensure that risks to critical cyber systems are identified and managed. This includes risks associated with supply chains and the use of third-party products and services.”
IT, OT and IoT in harmony
Some executive teams may be in the habit of thinking about cybersecurity mainly as an IT problem. But strong risk management practices integrate IT and OT issues with broader enterprise risks.
Thinking holistically about IT and OT risks is especially important in the context of operations that use smart devices to streamline production and other processes. OT systems running operational environments are often older and insecure by design but are connected to business networks that are constantly under attack. This presents challenges for traditional security models and will become more pressing as cloud services expand across IT and OT environments, further increasing connectivity as operations modernize. Engineering and operations will need to collaborate with security and technology teams during system selection and planning to integrate security and technology principles by design.
Manufacturers also need to understand the cybersecurity and risk implications for IoT devices they use on the factory floor—such as smart thermostats, sensors that detect production changes and various building automation technologies. These devices often need to be connected to both sensitive operational systems and the internet, complicating traditional security models.
Also important for manufacturers of these devices is the need to build in security by design to any IoT devices they manufacture and sell. Supply chain security risk management continues to raise the bar for the minimum security that customers expect of their IoT vendors, making security design a key component of product strategy.
Connectivity among IT, OT and IoT systems, and integrating them with business risk management, is essential to enabling accurate data analytics, remote support and overall efficiency.

