Hackers have initiated a wave of phishing attacks to try and capitalize on the fear and uncertainty related to the COVID-19 pandemic. As typically happens in times like these, the phishing threat has evolved and become more sophisticated as cybercriminals and nation states determine what’s working and make communications seem more authentic and believable.
Here are three specific ways that we are currently seeing threat actors attempt to weaponize the COVID-19 pandemic:
- Cybercriminals will use legitimate branding of a trusted organization such as the World Health Organization or Centers for Disease Control and Prevention to lure victims into clicking their phishes. Criminals buy domains that resemble such trusted organizations (i.e., cdc-gov.org, cdcgov.org, etc.) to perform phishing attacks.
- A range of malware, including both ransomware and remote access Trojans (RATs), is being delivered by COVID-19 phishing emails targeting most industries—in particular, finance, health care, life sciences and manufacturing.
- Phishing emails commonly contain a weaponized Microsoft Office document that when opened and executed installs malware or exploits a known vulnerability on the victim’s computer.
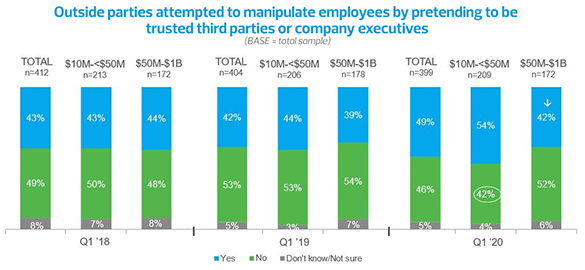
In RSM’s upcoming 2020 Middle Market Business Index Cybersecurity Special Report, we find that 49% of middle market executives say that outside parties attempted to manipulate their employees by pretending to be trusted third parties or high-ranking executives, a 7% increase over last year. These are the same attacks that criminals are deploying in conjunction with the COVID-19 pandemic, and the threats are unrelenting and potentially very harmful.