Field validations are vital for BEAD program integrity and compliance.
Key takeaways
The focus is shifting from selection to verifying deployment on the ground.
Federal alignment requires consistent validation procedures and records.
As state broadband offices move forward under the National Telecommunications and Information Administration’s (NTIA) Broadband Equity, Access and Deployment (BEAD) Restructuring Policy Notice, field validations are becoming an increasingly critical step to program integrity and compliance. While much of the focus has been on subgrantee selection, eligible entities are preparing for the practical realities of verifying deployment activities on the ground. Field validations will require robust procedures, trained personnel and consistent processes to align with federal expectations. This alert highlights key considerations that state broadband offices should weigh as they refine their validation strategies in the post-restructuring environment.
RSM supports state broadband offices with BEAD program services, including compliance and monitoring with field validation and environmental compliance.
Broadband validation considerations
Network background and compliance validation
The NTIA’s BEAD Restructuring Policy Notice, issued on June 6, 2025, expanded the definition of priority broadband technologies. These technologies now include fiber-optic technology, cable modem/hybrid fiber-coaxial technology, low Earth orbit (LEO) satellite services and terrestrial fixed wireless technologies that use entirely licensed spectrums, entirely unlicensed spectrums or a hybrid of licensed and unlicensed spectrums, so long as the technologies meet the technical performance requirements in the notice of funding opportunity as redefined by the policy notice and the Infrastructure Investment and Jobs Act.
Broadband offices should adopt field validation measures and compliance and monitoring plans to meet the new guidance and address the unique risks of each technology. This document will focus on LEO and fixed wireless technologies.
LEO satellite internet background
LEO has emerged as a broadband technology particularly suited to serve costly, remote locations.
Source: realpars.com
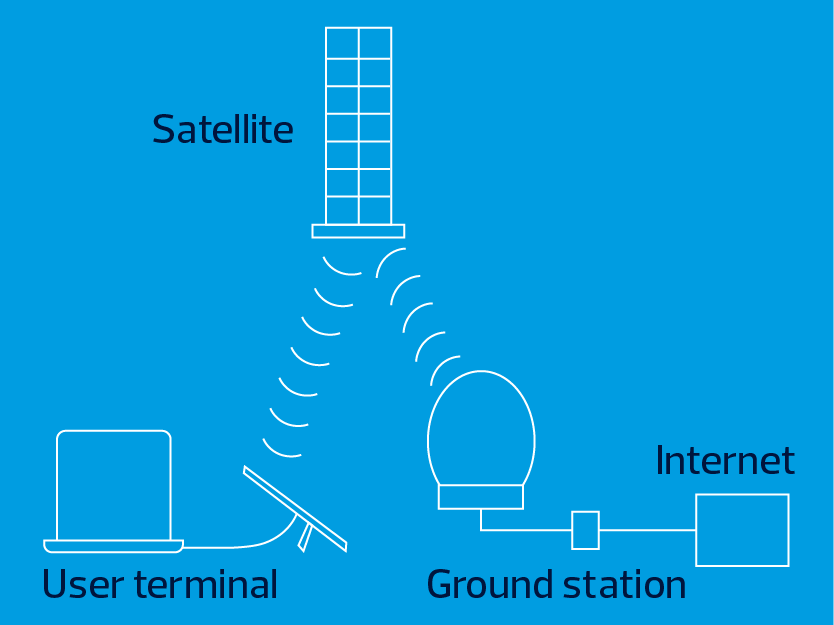
LEO uses small electronically steered dish antennas to connect customers to the internet through orbiting satellites. The antennas aim the electromagnetic signal at the satellite using a phased array, which rapidly shifts electron charges to form a tightly focused beam that can transition between passing satellites.
Intersatellite lasers then relay data to system gateways to backhaul traffic into terrestrial internet exchange points. Unlike fiber’s simultaneous two-way communication, LEO packets are sent in either download or upload, and continuous service is operated across multiple satellites. Funded equipment may include customer installation kits (i.e., antenna, modem, router, mount, power supply) and an allocation of satellite capacity for the 10-year federal interest period.
LEO uses small electronically steered dish antennas to connect customers to the internet through orbiting satellites. The antennas aim the electromagnetic signal at the satellite using a phased array, which rapidly shifts electron charges to form a tightly focused beam that can transition between passing satellites.
Intersatellite lasers then relay data to system gateways to backhaul traffic into terrestrial internet exchange points. Unlike fiber’s simultaneous two-way communication, LEO packets are sent in either download or upload, and continuous service is operated across multiple satellites. Funded equipment may include customer installation kits (i.e., antenna, modem, router, mount, power supply) and an allocation of satellite capacity for the 10-year federal interest period.
Fixed wireless background
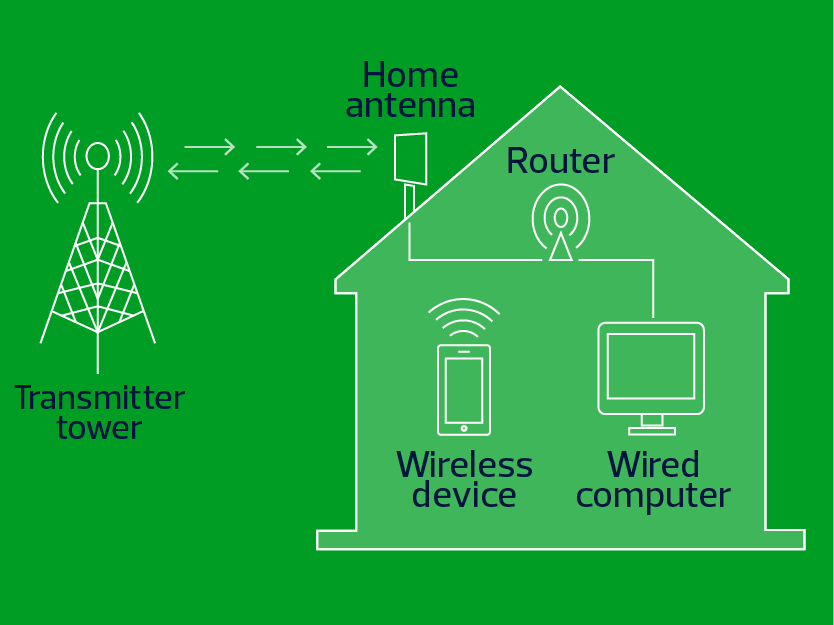
Fixed wireless broadband technology provides internet connectivity by transmitting radio signals between standalone or rooftop-mounted transmission towers and customer premises equipment. Towers are connected to the core network through a wireless or fiber backhaul.
Source: airbeam.com
Fixed wireless networks operate on licensed or unlicensed radio spectrums, which have different regulatory and operational considerations. For example, the policy notice details the methods to mitigate interference that unlicensed fixed wireless providers may face. Strategies range from peak-hour reserved capacity, conservative link budgets accounting for signal loss and antenna designs that manage signal interference risk.
Satellite and wireless technology–Validation and compliance
Validation and compliance measures vary based on fundamental differences in network infrastructure, network components, equipment and the risks of each technology type. The following chart depicts these differences.
Key considerations
| Consideration | Fixed wireless | Low Earth orbit |
Network equipment |
Tower, antenna, backhaul link |
LEO orbiting satellite, intersatellite links, ground stations |
In-home equipment |
Radio antenna, modem, router, mount, power supply |
Dish antenna, modem, router, mount, power supply |
Installation |
Line from router to antenna; potential for service quality degradation due to impediments and inclement weather |
Line from router to satellite dish with clear line of sight skyward; potential for service quality degradation due to impediments and inclement weather |
Congestion |
Time and frequency division duplexing, reserved capacity |
Subscriber to satellite capacity management |
Reliability |
Multiple input/multiple output alternative path routing |
Uninterrupted, continuous service through satellite mesh network transitions |
Validation and compliance*
*Where applicable under program requirements. Document as of Aug. 26, 2025.
Eligible entities should apply technology-specific validation procedures that fit each system’s network architecture and risk areas. This approach ensures that service commitments are fulfilled and that the program objective of reliable internet coverage is met.
RSM contributors
-
 David LukerPartner
David LukerPartner -
 Jen WadeDirector
Jen WadeDirector -
 Vince MassonDirector
Vince MassonDirector -
 Jaren MendelManager
Jaren MendelManager

